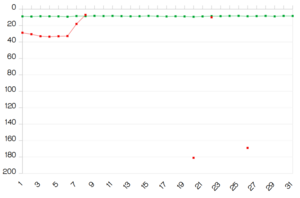
US government asks Microsoft to get its security right - before adding any new features.
China's Microsoft hack shows why security must always be prioritized over features and why there must not be a general key that can be used as a "backdoor".
What happened
In July 2023 a severe security issue in Microsoft's email servers was revealed. According to reports Microsoft lost a general login key to its entire email system which led to the US government being hacked. Supposedly malicious attackers connected to the Chinese government were able to siphon off ~60,000 emails from the US State Department, from the US ambassador to China, and from other US government officials’ mailboxes.
Microsoft itself did not detect the data breach, which was abused by China since mid-May 2023. Instead State Department officials were able to detect it themselves in June 2023, notifying Microsoft. What is more is that the US State Department was only able to investigate the breach because it used a more expensive Microsoft plan, which allowed access to logs - a feature that until then was not available in less expensive plans. Following the incident, Microsoft gave access to these logs to lower priced tiers of its product as well. This - at least - was the right move because in our opinion a security feature must not be locked behind a paywall!
Microsoft, the most valuable company in the world, was not able to detect the breach on its own. After being notified by US officials, security experts at Microsoft further investigated the data breach and found that Microsoft Exchange Online email accounts of 22 organizations and 503 individuals were affected by the attack. Their findings revealed that Chinese attackers from the so-called group Storm-0558 were able to gain access to a special security code that enabled them to access any email account on Microsoft. US intelligence revealed that the attack was carried out for one of Beijing’s most powerful spy services, the Ministry of State Security (MSS), which operates large nation state hacking operations.
Understandably, the uproar was huge, and the Department of Homeland Security announced it would initiate a Cyber Safety Review Board (CSRB) to review Microsoft's cloud security practices. The main task of the independent board was:
"The CSRB will assess the recent Microsoft Exchange Online intrusion, initially reported in July 2023, and conduct a broader review of issues relating to cloud-based identity and authentication infrastructure affecting applicable CSPs and their customers." ... "The Board will develop actionable recommendations that will advance cybersecurity practices for both cloud computing customers and CSPs themselves."
Report draws devastating conclusion for Microsoft
Now the independent Cyber Safety Review Board mandated by US President Biden has published its findings and it's bad, really bad.
The report comes to the conclusion that "the intrusion by Storm-0558, a hacking group assessed to be affiliated with the People’s Republic of China, was preventable." The data breach "should never have occurred."
The report raises strong concerns as Microsoft still does not know how exactly the Chinese were able to get access to the Microsoft Exchange Online mailboxes and accuses Microsoft of very poor cyber security practices, an intentional absence of transparency, and lax corporate security practices.
According to the report, Microsoft had made a "cascade of avoidable mistakes" which directly resulted from a poor security culture. For instance, the key used to access the email accounts should have been deactivated in 2021 already, and should never have the ability to access email accounts from the Foreign Ministry in the first place.
A Microsoft spokesperson told the Washington Post that
“recent events have demonstrated a need to adopt a new culture of engineering security in our own networks. While no organization is immune to cyberattack from well-resourced adversaries, we have mobilized our engineering teams to identify and mitigate legacy infrastructure, improve processes, and enforce security benchmarks."
The report, though, says this is not enough: Microsoft's “security culture was inadequate and requires an overhaul.”
Cascade of Microsoft errors
 Microsoft is the most valuable company worldwide, despite the fact of having a poor security culture.
Microsoft is the most valuable company worldwide, despite the fact of having a poor security culture.
The report highlights that multiple errors on Microsoft's side led to the Exchange mailboxes being vulnerable in the first place.
The old signing key used by the Chinese hackers to break into the system should have been disabled in 2016 already.
Microsoft should have switched from manual to an automated key rotation - which would have automatically disabled the old key - but didn't.
The key worked like a backdoor to consumer and business networks, which is in violation of security protocols.
One engineer from a firm acquired by Microsoft in 2020 was working on a compromised laptop and in 2021 accessed the corporate network from that machine. It's not certain that this laptop was the root cause, but Microsoft published an update in March 2024 which stated a “compromised engineering account” is the “leading hypothesis” for the cause of the breach.
Instead of letting this compromise go unnoticed, Microsoft should have run a proper security assessment of the firm's network after its acquisition - which it didn't.
All in all, this chain of errors shows that security is not the priority for Microsoft, which is what the report heavily criticizes.
It goes so far as to say Microsoft should listen to its founder Bill Gates who emphasizes the importance of security in a company email in 2002 already:
“In the past, we’ve made our software and services more compelling for users by adding new features and functionality. ... So now, when we face a choice between adding features and resolving security issues, we need to choose security.”
Risk to national security
The data breach caused by a lax security culture at Microsoft becomes even more severe when one considers that Microsoft is the major supplier to many governments - not just in the USA, but also in Germany and many other European countries.
The risk is not limited to Microsoft alone. Large cloud providers, such as Google, Apple, Amazon, and Microsoft, are lucrative targets for adversaries to Western nations and must focus on security. The report by the Cyber Safety Review Board finishes stating: “the entire industry must come together to dramatically improve the identity and access infrastructure. … Global security relies upon it.”
If malicious attackers are able to break into the email accounts of government officials, public authorities, possibly even intelligence services, countries like China and Russia can get their hands on very sensitive information, putting our national security in jeopardy.
And it looks like the adversaries have learnt about Microsoft's weaknesses.
In 2021, malicious attackers from China - again supported by the Chinese government - were able to compromise Microsoft Exchange email servers which affected at least 30,000 organizational accounts of business and government entities.
Also in 2021 the security specialist company Wiz disclosed a vulnerability in the Microsoft Azure infrastructure that made it possible for attackers to access, modify and delete data of thousands of Azure customers. Back then this was described as "the worst cloud vulnerability you can imagine" (while the Chinese hack of 2023 did top this one) as Wiz could access literally any database of Microsoft Azure customers.
But China is not the only adversary:
In January 2024, Russian attackers sponsored by the Foreign Intelligence Service (SVR) of Russia attacked Microsoft's corporate email service. Microsoft identified the attackers as Midnight Blizzard; they were able to break into mailboxes of senior executives and security employees.
In 2020, Russian hackers - again financed by the Russian government - were able to attack SolarWind's network software through which the Russian attackers siphoned off emails of at least nine US federal agencies as well as 100 companies. Following this attack Microsoft called for "the need of a strong and global cybersecurity response."
Unfortunately, the picture the CSRB report is now painting shows that Microsoft has not followed through on its own call for a better security strategy.
3 Lessons from the CSRB report
As the vulnerabilities of Microsoft's email service in the past five years have been dramatic, it's important to now focus on fixing the underlying issue: a lax security culture. We at Tuta are building an end-to-end encrypted email and calendar service with a clear focus on privacy and security. From our experience we can say that best security practices must include the following:
1. Security must always be prioritized over features.
This is a tough business decision because security in itself does not sell a product; features are required for this. But it is of utmost importance to fix vulnerabilities right away and to encrypt as much data as possible like in Tuta Mail. It is also great to see that the German government wants to enshrine the right to encryption into law. In Germany, the importance of security is being placed higher already, for example in Schleswig-Holstein. Germany's northernmost federal state is in the process of migrating from Windows to Linux, a great move in terms of security and digital sovereignty.
We at Tuta can fully agree to the conclusion of the report: Security must be prioritized over features.
2. General keys that can be used as "backdoor" must not exist.
The latest Microsoft Exchange hack was only possible because a general key was stolen by Chinese attackers which enabled them to login to Exchange mailboxes. This was a very lucrative backdoor for China, one that should have never existed in the first place. At Tuta we follow the strict security practice that private decryption keys are only accessible to the user, and never to us as the service provider. There is no general key to decrypt user data - and there must not be for security reasons. The absence of a general key that can be abused as a backdoor makes sure that a data breach like what happened with Microsoft in 2023 is impossible with Tuta Mail.
Our founder Matthias Pfau explains why this is important and why private keys must never be stored on a central server.
3. Security features must be available for free.
The Microsoft Exchange hack was only discovered by the US State Department because it has access to a logs feature - which was not included in lower priced tiers. At Tuta all security features are always available to all users, even when on free plans. This includes our brand-new post-quantum encryption as well as two-factor authentication for securing login credentials and session handling.
It is good that Microsoft has now given lower priced tiers access to the log feature as well, but it should have done so from the start.
In conclusion it truly does come down to what Microsoft founder Bill Gates said in 2002: It is important to prioritize security over features - not just for Microsoft, but for any cloud service provider.
The future will show whether this hack by China finally makes Microsoft establish a true security culture.
Until then, feel free to register a secure and encrypted mailbox with Tuta Mail.